People call those little things you connect to your cable or dsl modem wireless routers, but that's not really what they are. So what are they? They are part switch, part WAP(wireless access point), and part router. So you have four switch ports, and those are on one side of the routing and one port is for the internet which is on the other side of the routing. The WAP(Wireless access point) part is on the same side of the routing as the 4 switch ports, so all of that is behind the "router" which is doing Network Address Translation or NAT, which is actually what is protecting you. Well really we call it NAT but it's not really NAT, it's actually PAT or Port address translation. So your hiding behind a single IP and only if your computer makes connections to the outside can connections from the outside come in.
Your Network +++++++++++++++++++++++++++++++++++Intarweb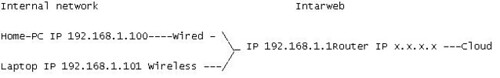
**Yes the router has two IP's, that's how routing works silly**
**And x.x.x.x is an IP assigned by your ISP**
I was asked how to get through, NAT which is to say PAT, which is a layer of security the router inherently gives it's users.
How do we break it so that connections from the outside can get in without having the internal network make the first move?
So the first thing isn't a hack, it's a feature of these "routers". It's called port forwarding and what it does, is it takes a port on a single computer on the internal network and puts that port directly on the internet. For example you start a home business running a website to sell candid shots of your girlfriend to the internet at large, or maybe you just want to have the candid shots and reap the benifits of having ads on the page selling the for 5 cents a click, well thats besides the point I don't care how your exploiting your girlfriend it's just important it gets done. Anyways so you have your site hosted on your home computer, you will have to forward that port to your computer with the webserver running on it. If you forward that port on your router to your computer, then that port on the home pc is exposed to the world and all can get to it. If anything is port forwarded on your router, and that software is vulnerable to an exploit, like the webserver you are using, evil hackers can break that software and get into your computer, or lets say you had 3389(RDP) port forwarded on your windows machine so that you could remote into it from the road, you know to add more pics of your girl, or other girls who you had told you worked for Girls gone wild and were wondering if they would like to audition for a paying part in the new magazine you aren't heading up. Well they could use TSGRIND or something else to brute force passwords.
So the evil hacker found your router and doesn't want to pay for your girl friends pics. The first thing he is going to do is a port scan probably with nmap and probably something like this:
nmap x.x.x.x -P0
**Being that x.x.x.x is your routers external IP**
**-P0 is saying don't send ping to check if the box is alive this is because most consumer grade wireless "routers" don't care about ICMP, becuase well I don't know it's really stupid, there used to be called this thing called ping of death, that could knock machines down, but all modern oses and these consumer grade devices are patched against this so I have no idea why they do this, if you ask me it's stupid becuase ICMP is a helpful troubleshooting tool. And proof that smart people still use it, ping google, you will typically get 3 out of four of your ICMP packets back, why don't you get one back, hell if I know I have some thoughts but I don't work for google and this post isn't about that. Also that is an capital p and a zero not a capital o.**
Ok so this nmap may return with some open ports, for the most part if the ports are described as open, they are probably forwarded. So that gives you, errr the evil hacker his current points of interest. Then if there was software behind those ports he would try to break it. Ok moving on...
How can I get in if all ports are blocked. Well if the router software itself is vulnerable I can use an exploit to break into it, and then use it to port forward inside of your network, or use it as a launching point for my nefarious deeds. How does the evil hacker do this....beyond the scope of this post.
Next issue, if you download any malware it can run on your local machine and then make connections to other machines on the intarweb that can then control or alter your machine. NAT obviously can't protect you from your stupidity. Don't download garbage or your fucked.
So the evil hacker knows where you live. Oh I know scary....well you shouldn't have filled out the domain information for your girl friends bestiality porn website accurately hackers use that stuff to figure shit like that out. So he drives to your house and he sits out side, well stupidly you left your wireless signal unencrypted, or you only used WEP...or smartly you used WPA, however your passphrase was a dictionary word....retard.
So he cracked your shit. Well why do you care. Because a very stupid company named Microsoft, in partnership with HP, made a protocol called SSDP. Why is SSDP stupid? Wiki says:
Quote:SSDP provides a mechanism which network clients can use to discover network services. Clients can use SSDP with little or no static configuration.
Wtf m8? Devices and software on your network CAN MAKE CHANGES TO YOUR FUCKING ROUTER. Meaning anyone who knows how to use ssdp can make a program that if launched on the inside of your network, whether from your machine or a malicious machine that is on your wireless network, can configure your router to portforward to whatever it chooses.
Thanks M$ we really love you.
Ok now that that's over, how do you guys like this style of post?
Saturday, December 13, 2008
Thoughts about hacking consumer grade wireless "routers".
Labels:
evil hacker,
hacker culture,
hacking,
hammer of god,
intarweb,
NAT,
networking,
nmap,
pat,
router,
routing,
ssdp,
switching,
tsgrind,
wireless router
Subscribe to:
Post Comments (Atom)
No comments:
Post a Comment